You’ve seen it happen. A colleague gets a strange email—maybe it looks urgent, maybe it comes from a familiar name, but something feels off.
In that moment, what choices do they really have?
Trust their gut and delete it
Take a risk and click
Or sit with the uncertainty, because asking for help isn’t quick or easy
As awareness professionals, we often tell people to “stop and think.” But what happens after that pause? Cybersecurity tools catch a lot, but not everything. Colleagues care, yet they don’t always know where to turn. And when support isn’t easy or trusted, even the most diligent person can be left second-guessing.
That’s the missing link in phishing defense—not employee vigilance, but the lack of easy, trusted support in the moment of doubt.
What’s missing in phishing defense
Phishing is still the number one human risk. The latest SANS Security Awareness Report shows it at the top of the cyber threat list, despite years of investment in security tools and training.
And with AI generating flawless emails, cloned voices, and convincing fake invoices, spotting the “bad” message is harder than ever.
Phishing attacks now arrive not just by email, but also as smishing (SMS), vishing (phone calls), whaling (C-level), or impersonation attempts on social media. Attackers use social engineering, spoofing, and fake domain names to trick people into giving up login credentials or sensitive information.
Anti-phishing technology blocks a lot, but not everything. When a suspicious message lands, it becomes a people problem—and a challenge for those of us guiding them.
The same report from SANS breaks down where and why many defenses break down:
Wrong focus. Phishing defense success is still measured by how many of your colleagues don’t click, as if vigilance alone could stop a threat that even seasoned professionals fall for.
Undervalued work. Awareness teams report being treated as “HR-lite” or compliance checkers, when in fact they’re the ones managing frontline human risk.
Unhelpful framing. Too many programs still treat people as the problem. This mindset produces “gotcha” simulations and annual refresher courses instead of building easy ways for people to ask for help in real time.
Barriers to speaking up. Reporting can mean filling out a clunky form, waiting days for feedback, or risking embarrassment if the message turns out to be safe. Faced with that, many stay silent.
The failure isn’t that people don’t care or can’t learn. It’s that the system doesn’t make it safe or easy for them to contribute. Until we fix that, phishing defense will keep falling short.
From problem to potential: turning people into early detectors
The best defense against email phishing isn’t about shaping “perfect” colleagues who never click. That goal is unrealistic and unnecessary.
What matters is creating systems of support, reporting, and feedback that people trust enough to use.
The state of reporting suspicious activity
According to studies by Verizon and Enisa, organizations that make it easy to check and report suspicious activity shorten the window between detection and response, reducing overall impact and cost. In other words, every report can be the difference between a near miss and a breach.
But reports don’t happen in a vacuum. People’s confidence in their ability to protect themselves is actually decreasing, and awareness of where or how to report remains low.
Underreporting is widespread, especially in smaller organizations, where people often worry about embarrassment or consequences if their suspicion turns out to be nothing.
For awareness professionals, this means shifting focus. The goal is not to count clicks or punish errors, but to create a supportive environment where colleagues see value in speaking up. Each report is a sign of engagement, and over time that engagement builds stronger defenses.
Every moment of doubt has value. When someone stops to wonder, “Is this message safe?”, that uncertainty can become useful intelligence.
If checking and reporting is simple and safe, those small signals add up. They help security teams spot patterns earlier, connect cybercrime incidents across the organization, and respond before damage spreads.
For awareness teams, each report of a suspicious email or text message is more than noise. It’s real-time threat intelligence that helps catch advanced threats like business email compromise (BEC) or spear phishing campaigns before they escalate into a full cyberattack.
Ordinary people can become one of your strongest defenses. But they only get there with the right scaffolding: clear channels, supportive feedback, and a culture that treats reporting as contribution, not confession.
– Erlend Andreas Gjære, Co-founder and CEO at Secure Practice
Building systems that turn doubt into defense
If uncertainty is valuable intelligence, then our job is to make it easy for colleagues to share it. That requires more than one-off campaigns or compliance modules.
It means creating practical systems of support that meet people where they are and give them confidence that reporting is worth the effort.
At Secure Practice, we’ve built our platform around three elements that make this possible:
1. Clear and accessible checking and reporting channels
With MailRisk, colleagues don’t need to guess how to raise a concern. A one-click button inside the mail client lowers the barrier and gives people a safe, visible way to act the moment something feels off. That clarity is what turns hesitation into action.
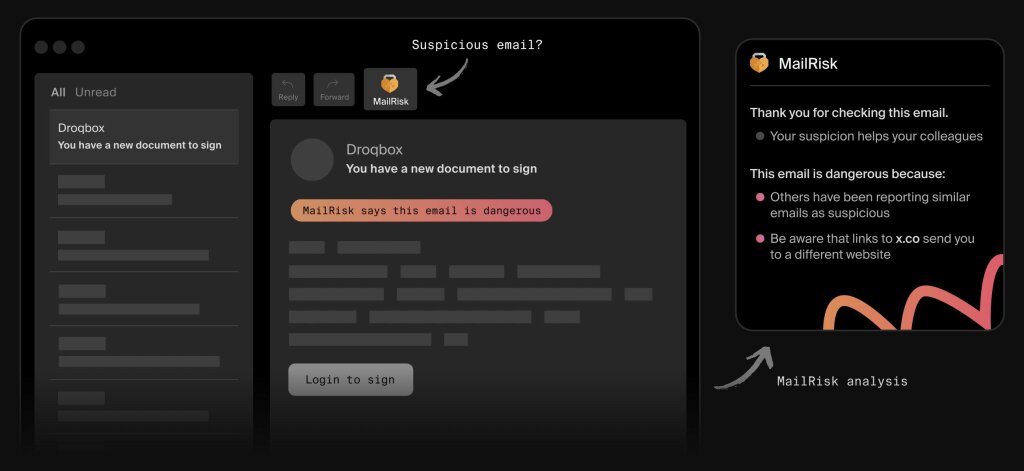
2. Immediate and supportive feedback
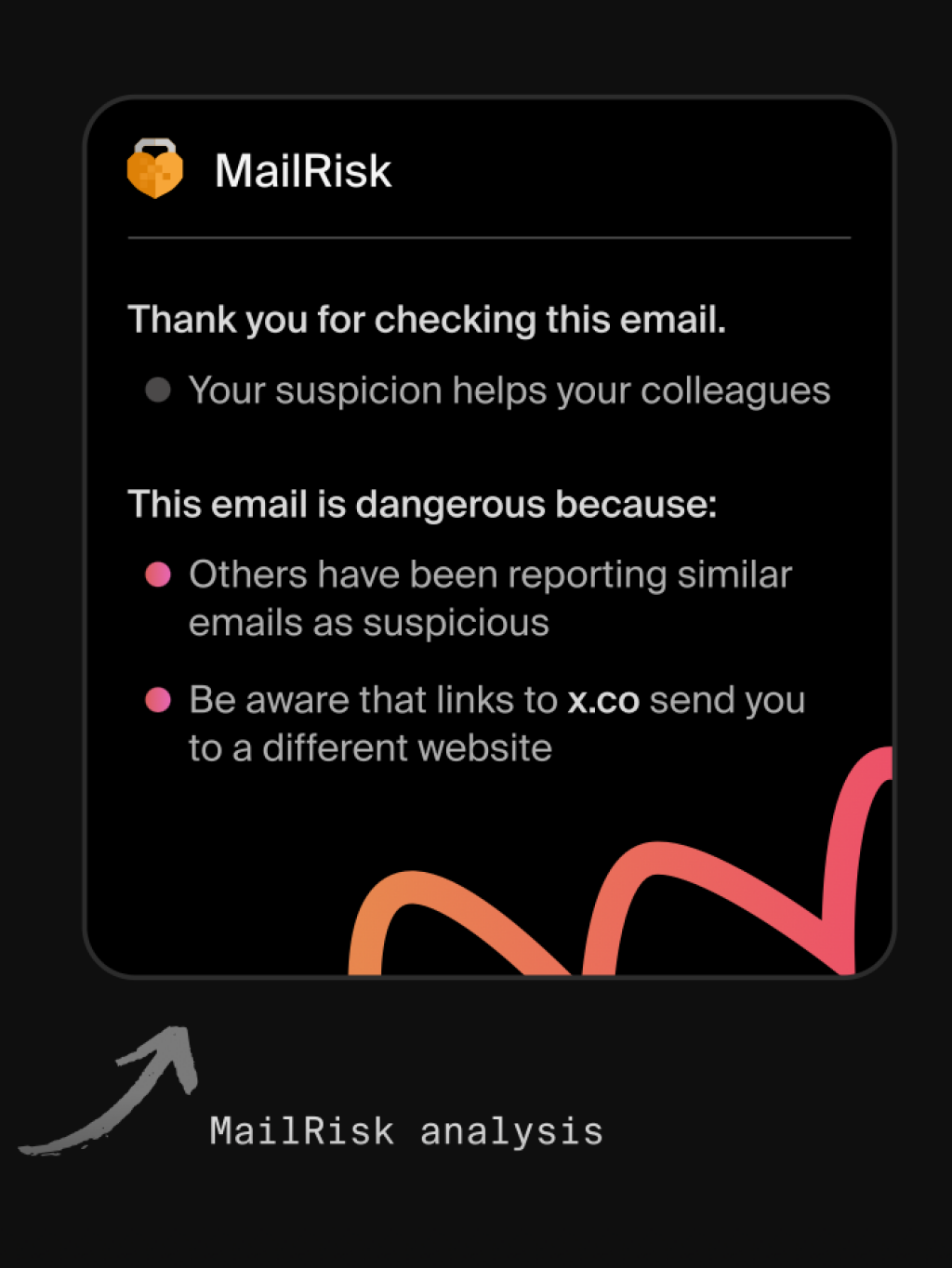
Silence after a report is the fastest way to lose trust. MailRisk gives colleagues instant analysis and feedback, so they know right away if the message was safe, malicious, or part of a simulation.
This transforms a report into a learning opportunity—without blame—and reinforces the habit of reporting.
3. Privacy-friendly metrics and follow-up
Awareness professionals need insight into patterns and risks, but colleagues shouldn’t feel like they’re being ranked.
MailRisk insights become even more valuable when combined with simulated phishing activities. Together, they provide a clearer view of behavioural patterns, without exposing individuals.
Anonymous data from these activities flow into human risk metrics that help you see where support is needed most. This way, you can focus on patterns instead of people, and guide learning where it makes the biggest impact.
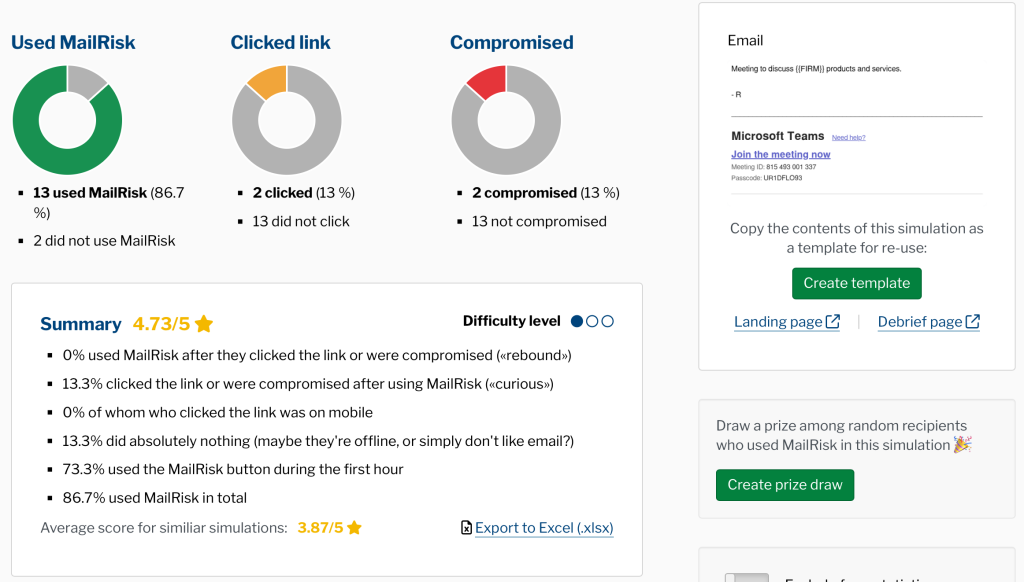
By focusing on metrics at the group level, you can see where support is needed most, while colleagues feel safe knowing they aren’t being ranked or singled out.
This approach respects trust while still giving security teams the data they need to act.
When these elements come together, phishing defense stops being a cycle of mistakes, blame, and silence. It becomes a shared responsibility—supported by technology, strengthened by people, and reinforced through everyday practice.
People found MailRisk instantly useful, and reporting rates went up. MailRisk lowers the threshold for getting help, but instead of creating more work for us, we are now almost completely rid of manual submissions to our helpdesk.
– Mari Nygaard Simonsen, Head of Threat and Vulnerability Management at Intility
From blame to support: redefining phishing defense
For years, phishing defense has been measured in clicks and failures, instead of in the moments when colleagues engaged, asked for help, and reported their doubts. As awareness professionals, you know this better than anyone. The missing link isn’t vigilance. It’s support.
Effective phishing defense is built on everyday habits, empathy for colleagues, leadership support, and tools that connect people directly to security.
That’s exactly why we built MailRisk:
To give people a safe, one-click way to check and report suspicious remails
To provide instant, supportive feedback so learning happens in the moment
To balance privacy and transparency: reports are not visible to peers or managers, but security teams can access the metadata they need, with access restricted to a small group
To help awareness professionals scale analysis, filter out noise, and focus on real threats
Phishing simulations, safe reporting, and feedback loops are the practices that change security behavior over time. When these elements come together, phishing defense becomes part of daily workflow, and security awareness turns from a cycle of mistakes into a system of support.
Phishing defense isn’t failing. It’s waiting for us to build systems that let people succeed.
Turn everyday uncertainty into a powerful defense system
We build tools and training that connect security teams with the workforce, turning human doubt into human defense.
FAQs about phishing defense
What is the best defense against phishing?
The strongest defense combines technology with people. Email filters and firewalls stop a large share of malicious messages, but some always slip through. That’s where human reporting and feedback systems matter.
Tools like MailRisk make this process safe and practical. This matters because phishing works when hesitation turns into silence. By making it effortless to report phishing messages, organizations close the gap that cybercriminals exploit. It’s a critical piece of email security that complements security solutions like email filtering, antivirus, and DMARC/DNS settings already in place.
When colleagues have a simple way to act on their doubts, and receive instant, supportive feedback, you build a second layer of defense that reacts faster than technology alone.
What are the 4 P’s of phishing?
The 4 P’s are Predict, Prevent, Protect, and Persist. This framework helps organizations anticipate attacks, stop them early with technical and organizational controls, safeguard people with supportive tools and security awareness training, and sustain defenses through continuous reinforcement. It’s not about a one-time fix, but about building habits and systems that last.
What are some effective strategies for phishing defense?
Short, one-off training isn’t enough. Effective strategies include year-round engagement, phishing simulations, and feedback loops that reinforce habits over time. This is where tools like MailRisk make a difference: each report comes with instant feedback, turning doubt into a learning moment.
Combined with privacy-friendly human risk metrics, awareness professionals get the insight they need to support colleagues without blaming individuals.
How does spear phishing work?
Spear phishing goes beyond generic scams. Attackers research their targets, often using real names, job titles, or ongoing projects, to make the message convincing. A single successful spear phishing email can compromise accounts, steal data, or move an attacker deeper into the network.
Awareness efforts should show colleagues how personalized attacks differ from generic ones—and give them a way to ask for help when they’re unsure.
How to identify phishing emails?
Red flags are often subtle. Watch for unexpected urgency, mismatched sender addresses, unusual links, or requests for sensitive information.
AI-generated phishing is making these harder to spot, which is why it’s important to give colleagues a way to check suspicions quickly. A one-click reporting button, backed by instant analysis, turns guesswork into clarity.
What are common signs of a phishing attempt?
Phishing messages often:
Have a sense of urgency (“act now” or “immediate action required”)
Contain errors in spelling, grammar, or formatting
Include suspicious links or unexpected attachments
Mimic trusted brands or colleagues, but with subtle differences
Make offers or requests that feel “off” compared to normal work communication
How can malware infect your computer?
Clicking a malicious link or downloading an infected attachment in a phishing email can install malware such as ransomware, spyware, or trojans. Once inside, attackers can steal personal data, capture credit card details, or move laterally through networks.
That’s why quick reporting of suspicious emails matters: it lets security teams block or contain cyber threats before they spread.
What tools can help prevent phishing attacks?
Cybercriminals exploit hesitation with phishing scams, fake websites, and malicious links that trick people into sharing sensitive data such as login credentials or credit card numbers.
A strong defense includes:
Email filters to block most malicious messages before they arrive
Multi-factor authentication (MFA) to protect accounts even if credentials are stolen
Reporting tools like MailRisk, which add a human layer, enabling colleagues to flag phishing attempts in real time so security teams can act before scammers exploit vulnerabilities


